Android / Nethunter
My passion for cybersecurity and pentesting led me to launch this project. I wanted easy access to a hacking environment anytime, anywhere.
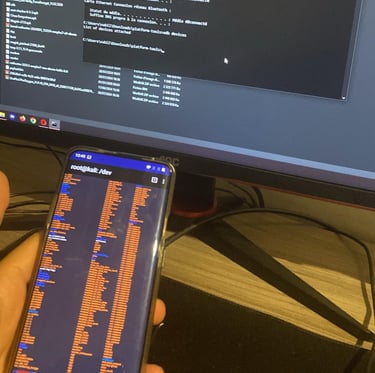
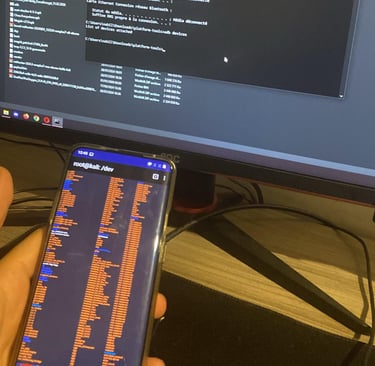
I bought a used OnePlus 7 Pro because it was one of the best phones compatible with a Nethunter kernel. First, I downloaded the SDK platform-tools, a set of powerful tools (like ADB and FastBoot) to control Android devices from my PC.
To unlock the full potential of Nethunter (e.g., Wi-Fi pentesting, which requires root access), I needed to root the phone. The phone originally ran Android 12, so I had to downgrade it to Oxygen OS 11 and a specific version for which the necessary .img files were available. I began by unlocking the bootloader and installing Qualcomm drivers on my PC to unbrick the phone in case I accidentally bricked it—a safety measure that proved useful since I had to try many times before succeeding.
Using Payload-Dumper-Go, Magisk, and several software files, I successfully achieved root access. With that done, I was ready to install Nethunter.
I started by installing TWRP and DM-Verify. After disabling DM-Verity, I booted into TWRP and installed the appropriate Nethunter version for my phone and Android version. Using Magisk, I installed Nethunter on the phone, then compiled and installed the Nethunter kernel using Kali Linux on my PC. Finally, I had a fully functional Nethunter phone with root access! The last step was disabling updates to maintain stability.
P.S: For added privacy, I bought a second-hand phone with cash, never inserted a SIM card, and never connected it to my personal network. This way, the phone cannot be traced back to me unless, of course, someone reads about it here :)
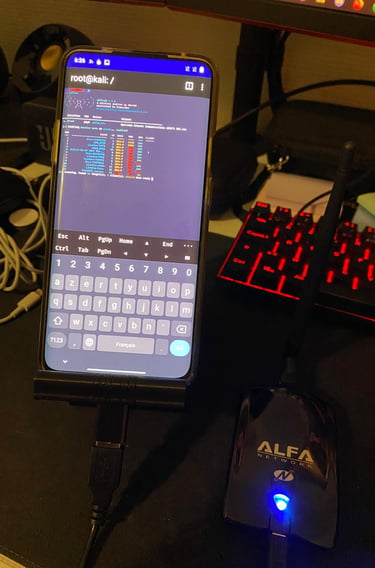
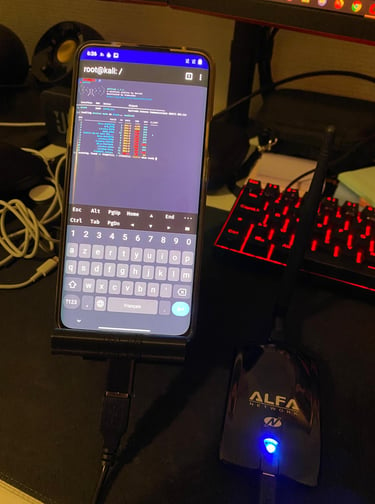


Here, I bought a wifi adapter that allows me to capture the handshakes for wifi pentest (EAPOL) and used wifite to launch an attack (I tried on my personal network, no networks were harmed in the process). Then i can crack the handshake with my pc (since I have a powerful GPU it would be faster)